Encrypted partition format
Encrypted DiskCryptor partition does not have visible signatures or any other identifiable data. Without knowing the proper password it is indistinguishable from random numbers, and the structure of the partition can only be discovered by providing right password.
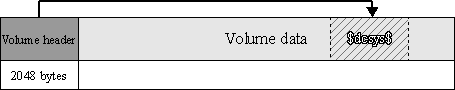
Encrypted partition has the housekeeping data area (volume header) that is followed by the user data.
Volume header
The first 2048 bytes of the partition are occupied by volume header. It contains the information about partition and keys to all user data. Volume header is encrypted with a chosen cryptographic algorithm in XTS mode, with a key derived from a user\'s password. User data that has been residing in the first 2048 bytes of a partition is moved to a relocation area, which is a contiguous sequence of sectors in user area (please read details below). Volume header does not have visible signatures, and without knowing the correct password is indistinguishable from random numbers.
Volume header format
typedef struct _dc_header {
u8 salt[PKCS5_SALT_SIZE]; /* pkcs5.2 salt */
u32 sign; /* signature 'DCRP' */
u32 hdr_crc; /* crc32 of decrypted volume header */
u16 version; /* volume format version */
u32 flags; /* volume flags */
u32 disk_id; /* unique volume identifier */
int alg_1; /* crypt algo 1 */
u8 key_1[DISKKEY_SIZE]; /* crypt key 1 */
int alg_2; /* crypt algo 2 */
u8 key_2[DISKKEY_SIZE]; /* crypt key 2 */
u64 stor_off; /* temporary storage offset */
u64 use_size; /* user available volume size */
u64 tmp_size; /* temporary part size */
u8 tmp_wp_mode; /* data wipe mode */
u8 reserved[1422 - 1];
} dc_header;| Offset | Size | Encryption | Description |
|---|---|---|---|
| 0 | 64 | No | Salt. Random number used when deriving volume header key. |
| 64 | 4 | Yes | DiskCryptor volume signature. Has the value of 0x50524344 (ascii \'DCRP\'). |
| 68 | 4 | Yes | CRC32 of the remaining part of the header (bytes 72-2047). |
| 72 | 2 | Yes | Header format version. Has the value of 1 for DiskCryptor 0.5 volumes. |
| 74 | 4 | Yes | Volume flags. Used for indicating volume\'s state. |
| 78 | 4 | Yes | Unique volume identifier. Used to search for a partition when choosing to boot from the specified partition. |
| 82 | 4 | Yes | Identifier of a main cryptoalgorithm, with which partition is encrypted. |
| 86 | 256 | Yes | Main encryption key of user data on a volume. |
| 342 | 4 | Yes | Identifier of an additional cryptoalgorithm, with which partition is encrypted. Indicates about a previously used cryptoalgorithm on re-encryption. |
| 346 | 256 | Yes | Additional encryption key of user data on a volume. Used for storing the previous key on re-encryption. |
| 602 | 8 | Yes | Offset in user data area, by which the first 2048 bytes of partition data have been relocated. |
| 610 | 8 | Yes | Size of a user data area. |
| 618 | 8 | Yes | Size of the encrypted area. Present only in a partially encrypted state. |
| 626 | 1 | Yes | Partition wipe mode used on encryption. Present only in a partially encrypted state. |
| 627 | 1421 | Yes | Reserved. Zero-filled. |
Relocation area
Relocation area - is a contiguous sequence of sectors where the first 2048 bytes of partition are stored.
Currently there are two methods of placement of this area that are being used: in $dcsys$ file, or at the end of partition. On encryption of partition that has data on it, this area is being placed in $dcsys$file, which is located in a contiguous sequence of clusters. On formatting a new partition, this area is being placed at the end of partition, after user data.
In order to protect the $dcsys$ file from being deleted, fragmented or moved, its access is forbidden by the driver.